A Client of our company had a problem, they got in an argument with their current IT Management company. Eventually the IT Management company wouldn’t give up the administrator account password of the complete domain. So this client was locked out of his own network. We were asked if there was a way to reset this password. So I started looking on the internet for some solutions.
The first one I tried in my own lab was the one that Daniel Petri describes in het Blog post at: http://www.petri.co.il/reset_domain_admin_password_in_windows_server_2003_ad.htm
There were some requirements for this trick.
- Local access to the domain controller (DC).
- The Local Administrator password.
- Two tools provided by Microsoft in their Resource Kit: SRVANY and INSTSRV. Download them from HERE (24kb).
The first one was no problem, but the second one in my case was a problem, we didn’t no the local administrator password.
So this is how I did it, first of all download the DART tools (Diagnostics and Recovery Toolset) from the Microsoft website, this is available for MDOP License owners. See http://www.microsoft.com/windows/enterprise/products/mdop/dart.aspx
There are other ways to get your hands on this tool, go to the Technet site and get a Technet Subscription. And if you don’t have access to both sources, go search Google.
I restarted the domain domain controller, and boot into the DART tool. Go to the Locksmith tool, and reset the password of the Administator account. Reboot the server, in Active Directory Recovery mode. This is important because now the Local accounts are available for logon. The local accounts are disabled on a Domain Controller, this is by design. In recovery mode logon with your new local Administrator password. Now do the trick that Daniel Petri describes in his post.
This is how it works globally.
Step 1
Restart Windows 2003 in Directory Service Restore Mode.
Note: At startup, press F8 and choose Directory Service Restore Mode. It disables Active Directory. When the login screen appears, log on as Local Administrator. You now have full access to the computer resources, but you cannot make any changes to Active Directory.
Step 2
You are now going to install SRVANY. This utility can virtually run any programs as a service. The interesting point is that the program will have SYSTEM privileges (LSA) (as it inherits the SRVANY security descriptor), i.e. it will have full access on the system. That is more than enough to reset a Domain Admin password. You will configure SRVANY to start the command prompt (which will run the ‘net user’ command).
Copy SRVANY and INSTSRV to a temporary folder, mine is called D:\temp. Copy cmd.exe to this folder too (cmd.exe is the command prompt, usually located at %WINDIR%\System32).
Start a command prompt, point to d:\temp (or whatever you call it), and type:
instsrv PassRecovery "d:\temp\srvany.exe"
(change the path to suit your own).
It is now time to configure SRVANY.
Start Regedit, and navigate to
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\PassRecovery
Create a new subkey called Parameters and add two new values:
name: Application
type: REG_SZ (string)
value: d:\temp\cmd.exe
name: AppParameters
type: REG_SZ (string)
value: /k net user administrator 123456 /domain
Replace 123456 with the password you want. Keep in my mind that the default domain policy require complex passwords (including digits, respecting a minimal length etc) so unless you’ve changed the default domain policy use a complex password such as P@ssw0rd
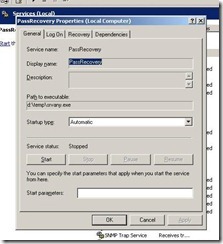
Now open the Services applet (Control Panel\Administrative Tools\Services) and open the PassRecovery property tab. Check the starting mode is set to Automatic.
Go to the Log On tab and enable the option Allow service to interact with the desktop.
Restart Windows normally, SRVANY will run the NET USER command and reset the domain admin password.
Step 3
Log on with the Administrator’s account and the password you’ve set in step #2.
Use this command prompt to uninstall SRVANY (do not forget to do it!) by typing:
net stop PassRecovery
sc delete PassRecovery
Now delete d:\temp and change the admin password if you fancy.
Done!
Disclaimer.
The information in this article is provided “AS IS” with no warranties, and confers no rights. This article does not represent the thoughts, intentions, plans or strategies of my employer. It is solely my opinion.